How Cybercrime Has Gone Mainstream

An excellent new paper from Raj Samani and Francois Paget of McAfee, a security technology company, explains how cybercrime has left the domain of the highly technical, brainy super criminals and has become quite commonplace. Indeed, the researchers show how the cybercrime industry has entered the “as-a-service” phase, which “extends well beyond hiring individuals to undertake specific tasks (for example, coding an exploit), with a broad variety of products and services available either to buy or rent”.
The researchers segment the “Cybercrime-as-a-Service” marketplace into four categories — Research-as-a-Service, Crimeware-as-a-Service, Cybercrime Infrastructure-as-a-Service and Hacking-as-a-Service — and explain how each of these submarkets functions, both individually and as a part of the whole. The end result, the authors argue, is “the emergence of a whole new breed of cybercriminal”, one who doesn’t need any technical expertise or even a computer; all they need is a credit card. Unsurprisingly then, the researchers expect the volume of cyberattacks to increase. Let’s take a closer look at the paper.
Research-as-a-Service
This is a category that includes the identification of so-called “zero-day vulnerabilities” — previously unknown vulnerabilities in a software application; when exploited, the attack occurs on “day zero” of awareness of the vulnerability. It turns out that these are not exclusively provided by illegal sources, as there are many legitimate “commercial companies that provide the sale of zero-day vulnerabilities to organizations that meet their eligibility criteria.” However, there are also “individuals who act as middlemen, selling such intellectual property to willing buyers who may or may not have the same strict eligibility requirements”. And the price could be quite steep, as shown in the table below:
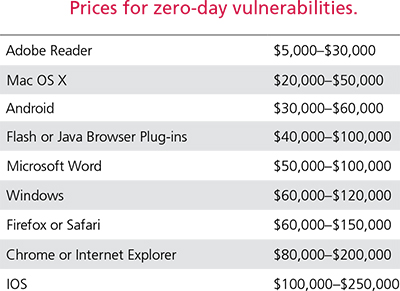
Moreover, the researchers tell us, whereas six years ago the market for zero-day vulnerabilities was not openly accessible, today money is the only restriction.
Crimeware-as-a-Service
Whereas Research-as-a-Service may be conducted legally, Crimeware-as-a-Service tools are exclusively available on the underground market. These include the development of code needed to exploit specific vulnerabilities, translations to enable non-native speakers to communicate with potential victims, malware services, exploits to take advantage of the identified vulnerabilities, as well as hardware that may be used for financial fraud (such as card skimming) or equipment for hacking into physical platforms.
The illustration below shows sales of exploits, including details of the targeted system, a brief description and the price, which, we are told, is closely aligned with the potential impact of the exploit. High-impact exploits are approximately three times as expensive as the low / moderate types.
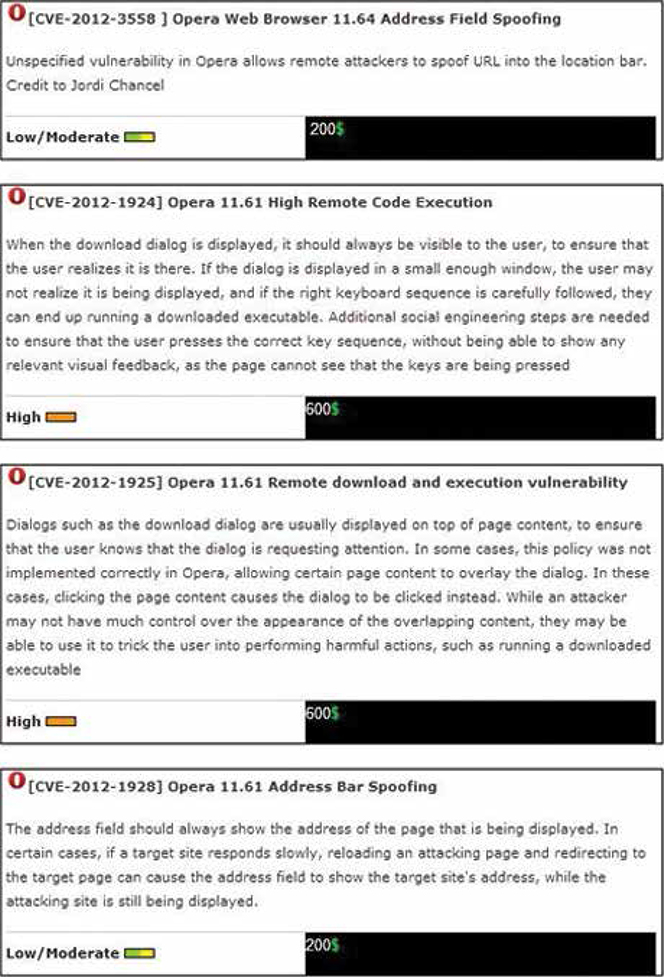
Also available are exploit packs for encryption services used to conceal an attack and avoid detection, as well as services for checking files against security software, which help cybercriminals make sure that all of their hard work is not blocked at the first hurdle by antivirus software. For example, there are services that allow criminals to test their malware against 35 antivirus solutions. Additionally, there is a service that tests the sending domain against a known list of domain blacklists. Crimeware-as-a-Service providers have also benefited hugely from the falling cost of cloud computing. One such provider, singled out in the report, offers to check anti-virus systems at a cost of $30 per month and $0.15 per check.
Cybercrime Infrastructure-as-a-Service
Once they have tested and acquired the necessary tools, cybercriminals need to find a way to deliver their attacks to the intended victims and a number of services allow them to do just that. Such services range from the availability to conduct denial of service (DoS) attacks to hosting malicious content. A prime example is the robot network, or botnet, which is a network of infected computers under the remote control of an online cybercriminal. The botnet can be used for sending spam, launching DoS, and distributing malware. The figure below lists the cost of renting various botnet service packages.
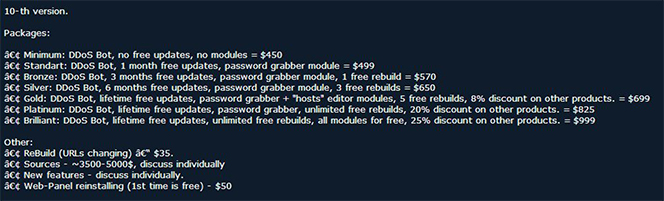
A critical component of the cybercrime infrastructure is the hosting service. It turns out that there are specialized service providers — called “bulletproof” hosting providers — which knowingly provide hosting or other related services to cybercriminals, “intending to ignore complaints by turning a blind eye to the malevolent use of their services”. One such service provider, named Matad0r, offers three levels of service, ranging from $50 per month to $400 per month, based on the specification of the system provided. I was quite taken aback by the low cost of what must be an illegal service (at least in the U.S.), but then the authors claim that there exist “a myriad of hosting services”, so I guess there are plenty of locations around the world where “bulletproof” hosting providers can hide.
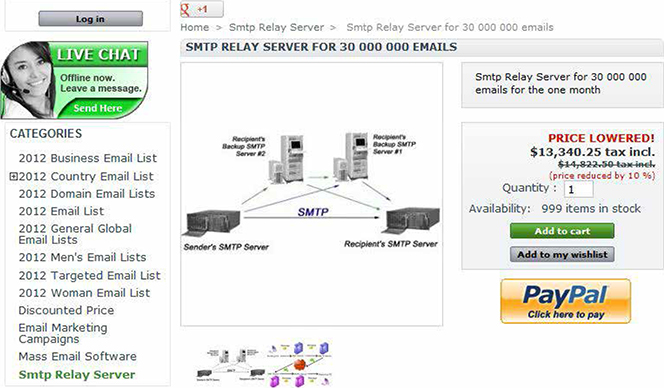
Then there is the matter of delivering the spam emails and this turns out to be the most expensive part of the operation. The illustration below shows a service claiming to be able to deliver 30 million emails per month for the price of $13,340.25. You will note that the payment option is as mainstream as they get.
Hacking-as-a-Service
Finally, a well-heeled cybercriminal may outsource the whole process — conducting research, building appropriate tools and developing an infrastructure — and pay for a service that will do the whole thing for them. The figure below shows a price list for a “Cheap Professional DDOS Service”, which allows attackers to name the website against which they wish to launch a DDoS attack, decide how much they are willing to pay, and then initiate the service. DoS and DDoS (distributed denial-of-service) attacks send a huge volume of traffic to the victim, preventing them from conducting normal business operations.
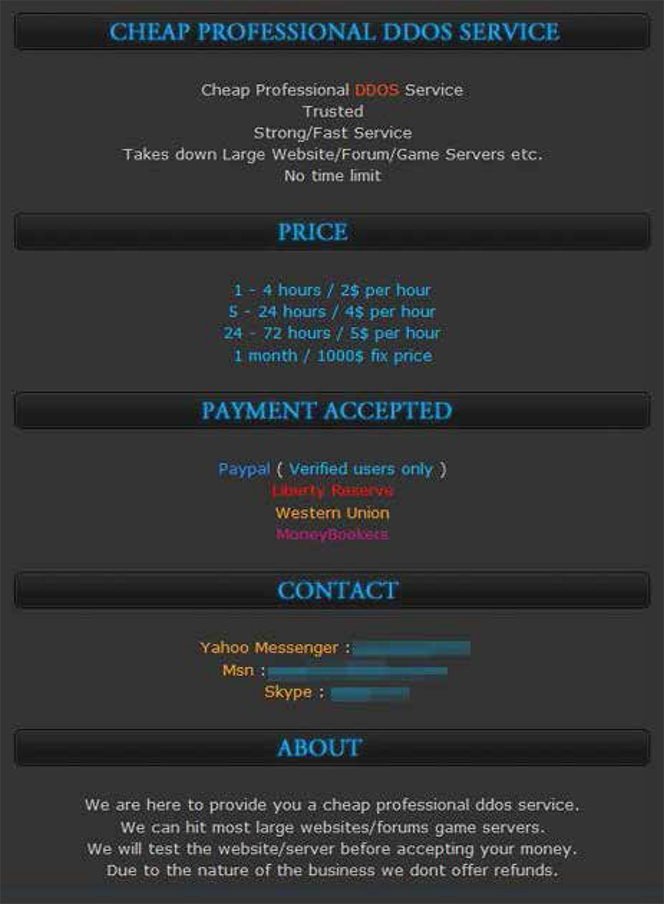
Once again, it is quite surprising to learn just how cheap the cost of the service is — you can launch a DDoS attack for as little as $2.
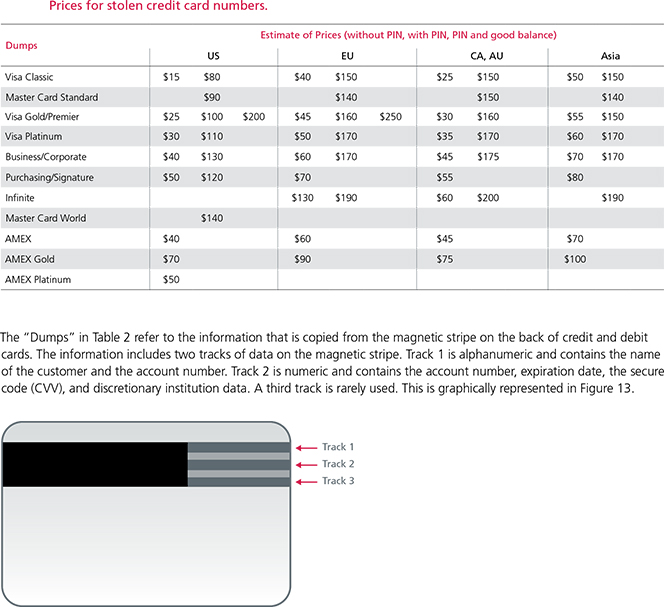
Perhaps the ultimate Hacking-as-a-Service offering is credit card information, which can be used either directly in card-not-present transactions (for example online purchases) or for creating actual plastic credit cards to be used at physical stores or, which is usually the case — at ATMs. Prices vary based on the completeness of the sold information and other factors.
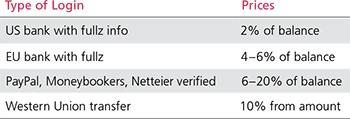
In addition to credit card information, available for sale are the log-in credentials for online banking, which are potentially even more valuable to criminals. Pricing varies from 2 percent to 20 percent of the available balance, as seen in the table below.
The Takeaway
Here is how the researchers summarize their findings:
This report offers readers a snapshot of the cybercrime market and how its services-based nature supports new entrants who do not require technical expertise. All that the modern cybercriminal needs to provide Cybercrime as-a-Service is a means with a payment method. We are witnessing the emergence of a whole new breed of cybercriminal. As a result, the volume of cyberattacks is likely to increase, and current trends and data suggest that this is exactly what we are seeing today.
The good news is that many are seeing the cybercrime threat as an opportunity for legitimate business. In a recent coverage of the issue, The Economist told us that there are now more start-ups in the data security area “than at any time in recent decades”. The same article reminded us that in his state-of-the-union address the U.S. president “decreed that America’s cyber-defences should be strengthened by the increasing of information sharing, and the development of standards to protect the country’s national security, its jobs and its people’s privacy.” We’ll see how that will turn out in practice.
Image credit: Flickr / marsmet481.


