These Hackers Are So Sophisticated, It’s Scary… And Yes, They’re Out To Get Your Credit Card.

If you can get scammed, you will be, a new report on cybercrime and stolen data just published by the RAND Corporation, a think tank, informs us. The cost to enter the black market of hacked data is already low and falling, even as the level of sophistication of the participants is increasing, we learn. Law enforcement is trying to keep up with the criminals and the number of takedowns is indeed increasing, the authors note, yet the black market is growing at an accelerating rate, the players are continually getting more creative and innovative and seem to be winning the struggle.
The paper’s bottom line: the black market for stolen data will keep growing, continue to innovate and adapt and continue to mature. Yes, the criminals will suffer a setback every now and then along the way and some of them will end up serving jail time, but such events, highly publicized though they will be, will do little to change the long-term trend.
If such a conclusion sounds defeatist to you, I guess the authors’ reply might be that this is simply where their analysis leads them and if the outlook looks bleak, well, that’s not their fault. For my part, I am inclined to accept the paper’s conclusions. We’ve been fighting hackers for about two decades now, employing all kinds of data security measures, devising rules, guidelines and best practices and yet, if anything, data heists seem to be increasing in frequency, becoming ever more sophisticated and are pulled off on an ever larger scale. Helpfully, RAND’s paper features a nice chart, which lends support to this observation. Let’s take a look at the research.
Mules, Experts and Administrators
Black markets for stolen data, just as their mainstream counterparts, consist of buyers, sellers and intermediaries, with varying levels of reliability and expertise, we are told. In another similarity, moving up the ladder is heavily reliant on personal relationships. And just as is the case with every mainstream market, this one has its unique features.
Within the black markets in question, we learn, there are hierarchies and specialized roles. The “administrators” occupy the top of the food chain, followed by experts with sophisticated knowledge of specific areas (for example, root kit creators, data traffickers, etc.). One level down the pyramid are the intermediaries (brokers) and vendors and then we have the “general members”, who, though at the bottom of the food chain, facilitate the all-important function of cashing out.
These general members, known as “mules” are the ones charged with turning the stolen credit cards or e-commerce accounts into usable money, for example, completing wire transfers and shipping goods bought with stolen funds. Mules can be either witting participants (fully aware of what they’ve gotten themselves into) or unwitting (as the paper describes them, “na?»ve individuals duped into involvement”. Here is a visual representation of the participation pyramid.
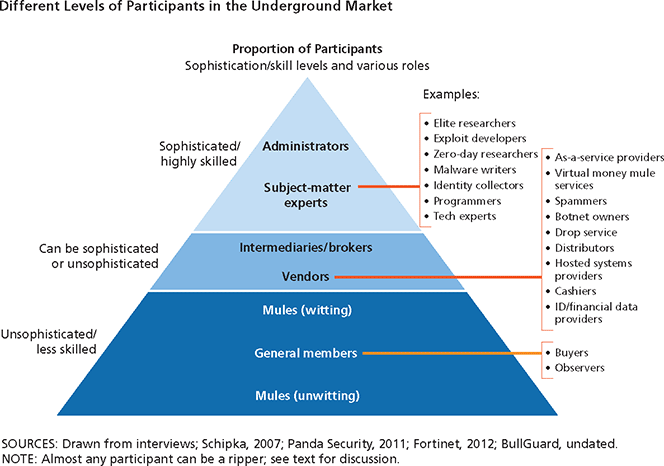
In general, the authors tell us, those higher up in the hierarchy (especially of the card and data rings) are rewarded the best. However, you can do pretty well, even if you are not at the top of the pyramid, provided you are close to the cash. The “witting mules”, for example, described as the “linchpin” of the system, due to their direct involvement in the actual disbursements of money, are singled out as occupying a particularly lucrative spot.
While there is a lower barrier to entry for the bottom tiers, we are told, accessing the top tier and getting involved in sophisticated crimes “requires personal connections and a good reputation, especially for being trustworthy”. Surviving a purge helps your reputation and “can be a badge of honor”.
Hacking-as-a-Service
The RAND researchers remind us that data hacking has entered the “as-a-service” stage, an observation we’ve previously reported on. As-a-service offerings continue to grow in popularity, we are told, “as new products and technologies burgeon”:
The market demands more specialized, user-friendly, as-a-service models with easy-to-use interfaces, allowing more participants, regardless of technical ability, to enter the market and get involved—they simply pay for installation and have a service do the work.
And the supply is there to meet the demand. Moreover,
Vendors often guarantee their products’ lifespan or value—for example, guaranteeing a particular malware variant is good for ten hours before detection by antivirus products, or that a credit card is good for a certain amount of money—and some can track what a customer does with their product to make sure “terms of use” are not broken—a sort of “digital rights management.”12 For example, a vendor might label and track each install sold, with the ability to shut down anyone who is making too much noise by infecting too many victim machines.
So this surely looks like a mature, highly sophisticated market. And the “products” in question—the exploit kits—are quite affordable. For example, the cost of hacking into accounts can vary anywhere from $16 to more than $325, depending on the account type, we are told, and the researchers give us a long table listing the price tags of the various types of hackware.
The cost of data also varies, based on a number of factors. For example, when the supply is abundant, as right after a big data breach, prices fall precipitously, as one would expect. After the Target breach, we learn, prices fell from $15 – $20 per record to $0.75 per record. Similarly, credit card data may cost $20 – $45 per account when supply is limited or the data are freshly acquired or it could be $10 – $12 if the market is flooded. Additionally, no-limit cards (such as the American Express Black card) and chip-and-PIN cards are more valuable. European cards tend to fetch higher prices than American ones for reasons we’ve discussed previously.
The Rise of the Data Heist
The authors write at some length about law enforcement’s increasing sophistication and successes, listing their notable successes: Liberty Reserve, Silk Road, Carder.su, etc. Yet, just a brief look at the chart below tells a story of a losing battle. Despite the authorities’ best efforts, data breaches are becoming increasingly more frequent.
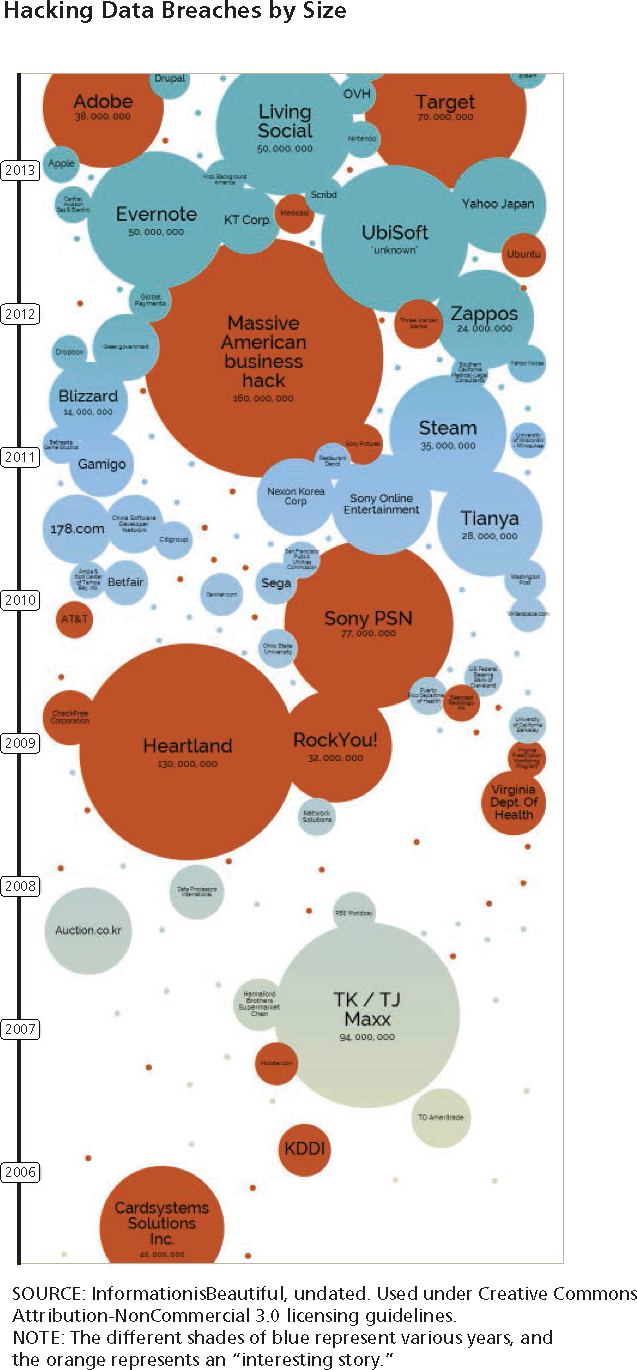
And the real picture may be even more disturbing. As the authors caution, and that has been noted by many other researchers before, there is an underreporting of data breaches, so a majority of them never get disclosed, as victims try to protect their reputation.
The Takeaway
So where does that leave us? Well, here is how the RAND researchers see it:
[D]espite the growing rate of takedowns, the black market remains resilient and is growing at an accelerated pace, continually getting more creative and innovative as defenses get stronger, law enforcement gets more sophisticated, and new exploitable technologies and connections appear in the world. Products can be highly customized, and players tend to be extremely specialized.
The black market, once a varied landscape of discrete, ad hoc networks of individuals motivated by ego and notoriety, has now become a burgeoning powerhouse of highly organized groups, often connected with traditional crime groups (e.g., drug cartels, mafias, terrorist cells) and nation-states.…
We can expect the underground market to continue to grow and be more relevant, continue to innovate and adapt, and continue to mature.
As I said, not a bright outlook.
Image credit: Wikimedia Commons.


